Abstract
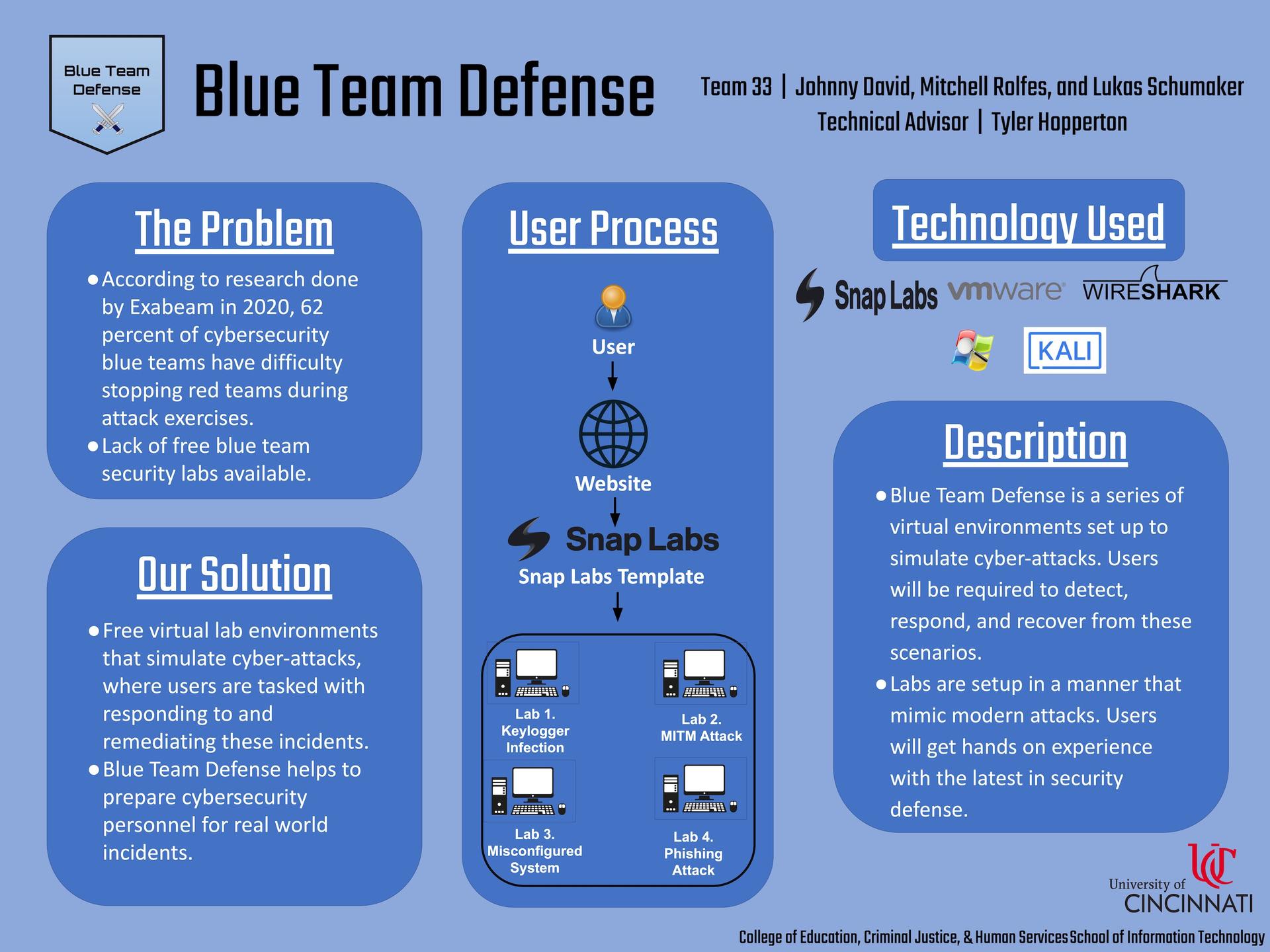
Exploiting systems using known vulnerabilities has become a concern for companies. So much so, penetration testers are being offered lucrative contracts to find vulnerabilities and exploits on a company’s system. Our team noticed there were many training programs for these testers, known as “red-team,” to hone their penetration skills and be the offense. When looking for “blue-team” training programs, there are much fewer, making it difficult for IT professionals to train on how to defend against such attacks. Our team set out to create labs in which an attack has already taken place, and it is up to the user to diagnose the attack, research the incident, and return the system to its original state. Our goal was to create an environment that simulates real world attacks and give the user tools to take out the attack.
Members

Johnny David

Lukas Schumaker

Mitchell Rolfes
Advisor: Tyler Hopperton












